LEAPS RTLS
Is LEAPS RTLS an advanced version of PANS RTLS?
PANS RTLS can be considered a “Lite” version of LEAPS RTLS. Based on the experience with PANS RTLS, many changes and improvements have been made to create LEAPS RTLS.
The main focus was on improving system performance, improving security, adding flexibility using network profiles, and improving the data server and API.
Please see Comparison for more details.
How LEAPS is licensed?
LEAPS provides modules with LEAPS software stack and are offered at favorable market price. LEAPS software stack is licensed as binary code, non-transferable and royalty-free.
For specific projects where the modules cannot be pre-loaded with the LEAPS software stack, the binary code is licensed as non-transferable with a royalty fee per
For centralized systems where tracking is used, a LEAPS Server is needed. The pricing for LEAPS Server will be specified in the upcoming months. Please subscribe to our mailing list to get informed.
Is the hardware of LEAPS different from PANS?
The LEAPS software stack is designed to run primarily on the DWM1001 module, and the same applies to the PANS software stack. The stack is highly portable and can run also on different hardware.
A typical end-product device contains a board with power circuits, connectors, optional microcontroller and at the heart, there is a DWM1001 module with LEAPS software stack.

Can I use LEAPS to navigate and track nodes at the same time?
Yes, most network profiles allow multiple modes of location service. Depending on the selected network profile, the Tag’s position can be used in both navigation and tracking modes at the same time. The data are available via on-module and server API.
Please see the System Performance comparison for more details.
How many Anchors and Tags a LEAPS network can have?
The network stack is designed in the way that it always aims to reuse the air-time using an effective mechanism for both Anchors and Tags. In short, if a condition attenuates the signal of any transmitting node in a way that will not negatively influence transmission and reception by any other node then that air-time can be reused.
This allows virtually unlimited amount of nodes to be deployed in a spread area where this condition can be created. All of this happens automatically using effective mechanisms implemented in LEAPS.
What location techniques are supported in LEAPS?
LEAPS supports various locating techniques, including
TWR - Two-Way Ranging
UL-TDoA - Uplink Time Difference of Arrival
DL-TDoA - DownLink Time Difference of Arrival
Versatility makes it easy to balance the system requirements, costs, deployment time and maintenance complexity. Applications range from simple distance proximity, to high-speed tracking or navigation of an unlimited amount of receivers.
Can I send and receive user data on the edge nodes using LEAPS?
The Anchors and Tags can send and/or receive user data depending on the selected network profile.
Data sent from the Module toward the Server is called Uplink.
Data sent from the Server toward the Module is called Downlink.
Please see the System Performance comparison for more details.
How can I configure, receive and send data using a node?
LEAPS modules can be configured, and data can be handled using the following APIs
Bluetooth - New API over encrypted channel helps to handle data fragmentation commonly experienced on Bluetooth properly. The API is in TLV format andt supports the same command set used for UART, SPI and USB (in the future).
UART - TLV binary format
SPI - TLV binary format
USB - TLV binary format (in the future)
Shell over UART - Debug shell in human-readable format
Does LEAPS support wireless Ultra-wideband backhaul?
The system can support wireless Ultra-wideband backhaul depending on the selected network profile. The location and user data can be sent toward the Server and the nodes using Ultra-wideband radio.
There are two types of backhaul supported:
Non-routing UWB backhaul - This is a one-hop backhaul where a bridge-enabled device can forward the data between a Server over Ethernet and a node over UWB.
Routing UWB backhaul - This is a multi-hop backhaul where a bridge-enabled device can forward the data between a Server on Ethernet and a node on UWB. Other infrastructure devices can participate in forwarding the data with other nodes via UWB. Routing mechanism is fully automated and adaptive to the changes in the network.
Where the location and user uplink data are available?
The backhaul uplink location and user data are available via these APIs
Bluetooth - TLV binary format
UART - TLV binary format (limited data throughput)
SPI - TLV binary format
Data Server - MQTT protocol
What are the downlink events and commands?
They are service commands and events providing the following services via the Data Server.
Collection of the signal map between the Anchors - can be used for installation and debuggingg purpose.
Collection of distances between the Anchors - can be used for auto-positioning of the Anchors.
Remote control of GPIOs on the module.
and more.
How does security in LEAPS work?
The following security mechanisms are implemented in LEAPS
Secure key storage - the root of trust using hardware secure element.
Secure boot - to guarantee the consistency of the firmware.
Node authentication - nodes on the network are authorized using asymmetric authentication. The client’s key set is possible.
Key exchange - the network key is exchanged securely and automatically between the authorized nodes.
Node sign-up - Only authorized nodes can connect to the network when enabled.
Node access revoke - revoke access for nodes already connected to the network.
Encryption for UWB and Bluetooth communication - data frames sent via UWB and Bluetooth communication are encrypted using AES-128.
Data encryption is resistant against to attacks
Frame replay
Unauthorized nodes
Length extension attack
Data extraction when the AES cipher block repeats
Power interruption
DoS
A unique way to generate entropy uses network synchronicity which makes it very difficult to apply an attack even if the key is stolen.
Highly optimized for embedded modules with memory constraints.
Low data overhead being sent over UWB.
Changes in infrastructure detection - helps to detect when the infrastructure nodes have been moved.
Whole chain security - data are all protected from the input point until the output interface of the last component.
All communication via TCP/IP uses TLS 1.2.
The system should undergo penetration test in the future.
Is it possible to send data between the Anchors/Tags and the server?
Yes, depending on the profile, it is possible to send data from the Anchors or Tags to the LEAPS Server. There are two types of data.
Uplink - data from the Anchors and Tags to the LEAPS Server.
Downlink - data from the LEAPS Server to the Anchors or Tags.
Can I use the unused GPIOs on the module?
Yes, there are GPIOs available for your applications. They can be controlled via API - UART, SPI or MQTT.
What API interfaces are available?
LEAPS modules can be configured, and data can be handled using the following APIs
Bluetooth - New API over encrypted channel helps to handle data fragmentation commonly experienced on Bluetooth properly. The API is in TLV format and supports the same command set as used for UART, SPI and USB (in the future).
UART - TLV binary format
SPI - TLV binary format
USB - TLV binary format (in the future)
Shell over UART - Debug shell in human-readable format
What does LEAPS profile mean, and how is it unique from variant?
Variant is a pricing model. LEAPS modules are offered in 3 variants with different sets of supported networking profiles. The users can choose what would best fit their applications and budgets.
Profile is how the network protocol is organized. Each profile is designed to provide optimal performance for a specific type of applications. Depending on the variant, one or several profiles are supported. The user has to select the profile which best fits the application.
Is it possible to obtain the Tag Node (TN) position as well as the distances from all interfaces?
There is a difference in obtaining these values from Supported Interfaces:
Via BLE, UART, USB, or SPI, the user can obtain both the TN’s position and the distances.
Via MQTT, only the position is available.
Do Tags have data slots reserved for location and user data on Ultra-wideband network?
Depending on the selected network profile, the Tag data slot can be
Roaming - The Tags reserve data slots with the surrounding anchors using an effective mechanism that keeps reserving in advance the data slot as it moves around. This mechanism helps to avoid unnecessary collision, keep a high probability of data delivery and effectively releases the resources when the Tags no longer use it (e.g. when it is no longer in range or when the update rate decreases because it is staying still). This feature allows a virtually unlimited amount of Tags in the system when the Tags are spread over the area. When a certain amount of Tags is in range with each other and running at the maximum update rate, the maximum network capacity is achieved.
Dedicated - The Tags get data slots reserved automatically during its sign-up to the network. The data slots are dedicated and will expire only if the Tags no longer uses it. This is suitable for fast tracking applications where it is necessary to guarantee data delivery for the Tag on every update rate anywhere in the network.
Probabilistic - The Tags do not reserve data slots and their data delivery is based on a probabilistic model. This approach is suitable for applications where the Tags should achieve a very long battery lifetime.
Please see the System Performance for the details.
Is it possible to collect orientation data from a sensor and send them to the server?
Yes. There are two options to collect the sensor data and send them to the server:
Use an external MCU to collect the data from a sensor and then send them via the LEAPS Module using interfaces like UART or SPI.
We are planning to embed drivers for a few selected inertial sensors. The client only needs to connect the sensor to the dedicated I2C pins and enable it using simple commands. The data will be automatically collected and sent to the server at the required rate.
Does LEAPS support User Application?
No, contrary to PANS, LEAPS does not support User Applications, i.e. LEAPS does not provide a linkable library to create custom applications. For additional functions, there are two options:
It is necessary to use an external MCU.
We are planning to embed drivers for a few selected inertial sensors. The client only needs to connect the sensor to the dedicated I2C pins and enable it using simple commands. The data will be automatically collected and sent to the server at the required rate.
Is it possible to collect the battery level of the tags on the LEAPS Server?
There are two options to measure and send the battery level of the Tags to the server.
Measure the battery level using an external MCU and send it to the Server via the module interface.
We are planning to embed automatic battery voltage level measurement and send it to the Server.
How many Anchors can I install on my network?
For a network where the Anchors are installed following a certain rule, virtually unlimited amount of Anchors can be deployed over a spread area.
In a building-like area, this condition is easier to achieve. In an open-space area, it is necessary to keeping distance between the Anchors is necessary.
If all Anchors are placed in range with each other, a maximum of 30 Anchors can be connected to the network. The rest will wait until a free slot is available.
The Anchors form a network and solve the issues automatically.
Is Ethernet required for the Anchors?
Ethernet is required only if Tracking location mode is used. Depending on the selected network profile, it might be required on all Anchors or only on some. This flexibility allows to balance the system requirements, costs, deployment time and maintenance complexity.
How to force uninstall of LEAPS Android Manager application?
On Samsung Tablet: Settings -> Apps -> Storage (at the bottom) -> Applications -> LEAPS Android Manager -> Uninstall
What interfaces can be used for communication with the backend system?
When the gateway approach is used in tracking and data telemetry, LEAPS provides various connectors for communication with the systems on the internet network. The following connectors are currently supported.
MQTT version 3.1.1 or newer.
The following picture illustrates interfacing between LEAPS and internet network.
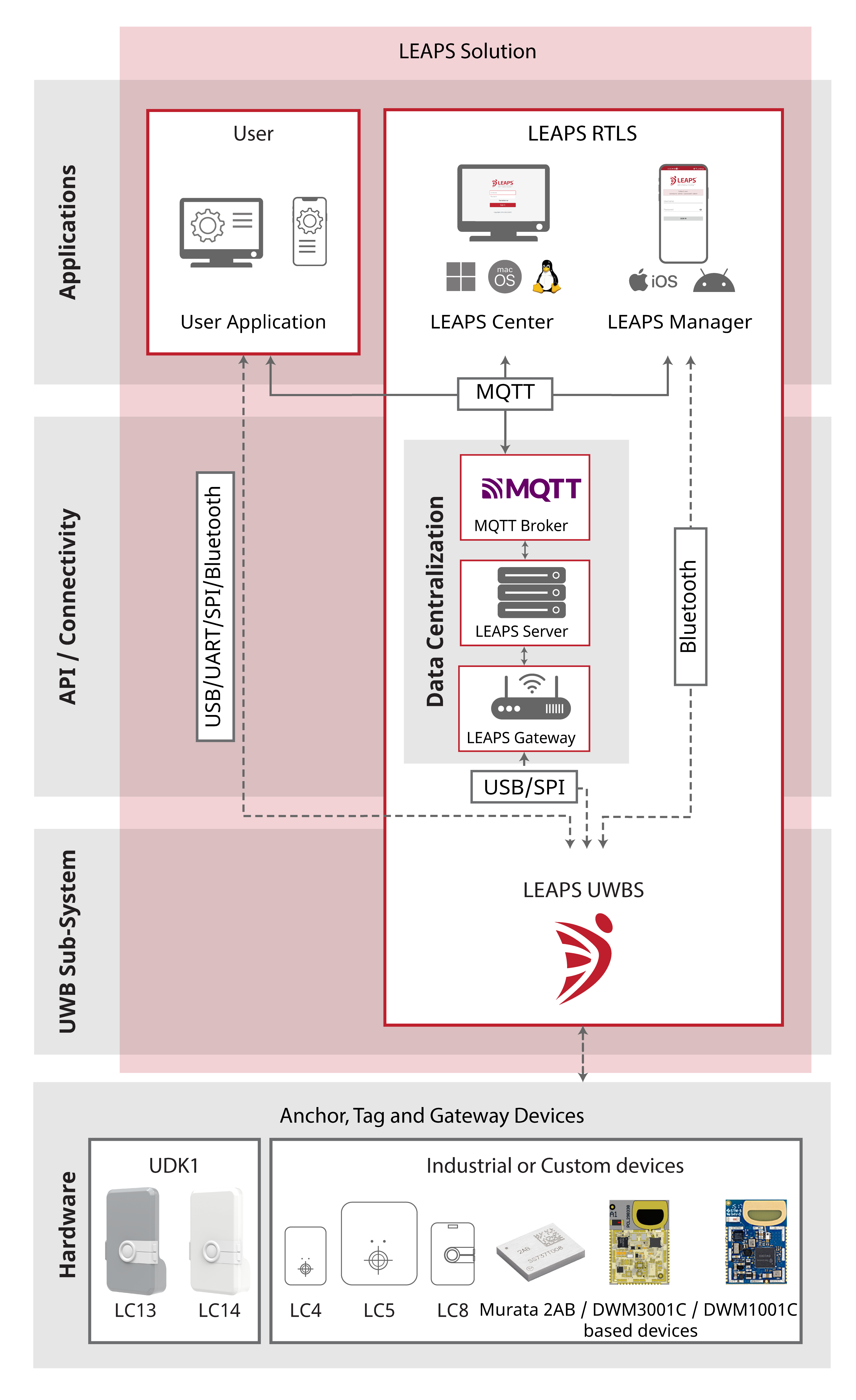
Why are there NaN position in the MQTT messages?
The MQTT messages with NaN are published when the tag could not calculate its position. This can happen in one of the following cases:
The Location Engine is disabled.
There were less than 3 measurements obtained -> the trilateration could not process the results.
The measured distances were so inaccurate that position could not be calculated.
The positions of the anchors are incorrect.